As an example let’s say we want to verify integrity of following file from https://hashcat.net/hashcat/
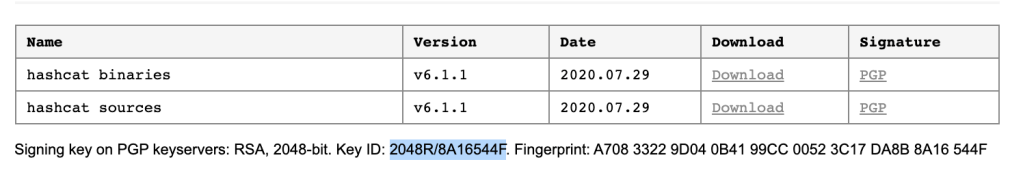
- First download the file and its PGP signature (ends with .asc)
$ wget https://hashcat.net/files/hashcat-6.1.1.7z.asc --no-check-certificate
$ wget https://hashcat.net/files/hashcat-6.1.1.7z --no-check-certificate
2. Next download and import the key from PGP keyserver with following command:
$ gpg --keyserver keyserver.ubuntu.com --recv-keys 8A16544F
gpg: requesting key 8A16544F from hkp server keyserver.ubuntu.com
gpg: /home/sjain68/.gnupg/trustdb.gpg: trustdb created
gpg: key 8A16544F: public key "Hashcat signing key <signing@hashcat.net>" imported
gpg: no ultimately trusted keys found
gpg: Total number processed: 1
gpg: imported: 1 (RSA: 1)
3. Now test the signature
$ gpg --verify hashcat-6.1.1.7z.asc hashcat-6.1.1.7z
gpg: Signature made Wed 29 Jul 2020 06:25:34 AM EDT using RSA key ID 8A16544F
gpg: Good signature from "Hashcat signing key <signing@hashcat.net>"
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: A708 3322 9D04 0B41 99CC 0052 3C17 DA8B 8A16 544F
To make the warning disappear we need to sign hashcat’s key with our private key. That will make it trusted. See https://security.stackexchange.com/a/147467/44139
